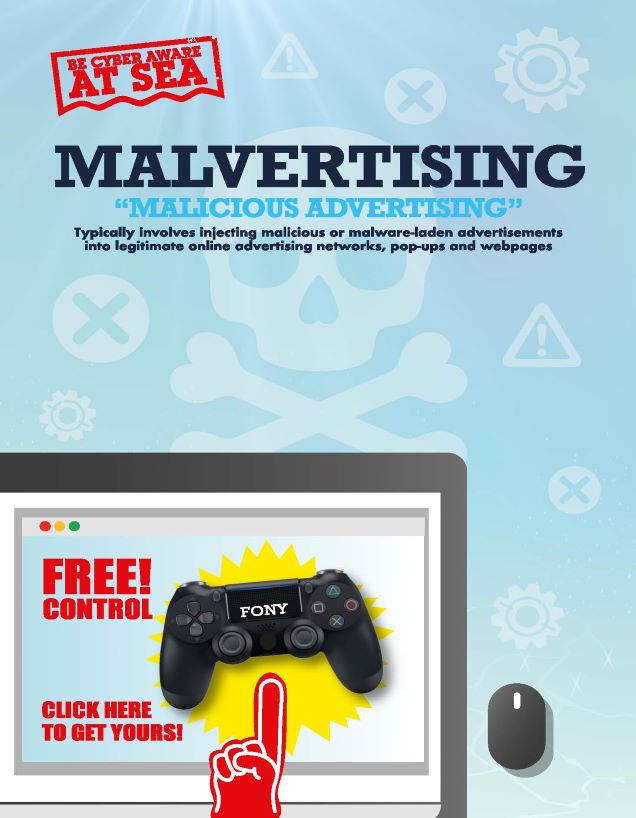
Malicious advertising or ‘Malvertising’ as it is known is used by hackers to distribute malware or direct the users to a malicious server. The hackers use several techniques to hide this malicious content in adverts across the web, which when clicked begin the process of infecting the user’s computer and network. Sometimes you do not even need to click on the advert!
The ads can appear anywhere online; banners ads, pop up, ads before videos so if you are online chances are you will come across a malicious advert.
Whilst the adverts generally appear on less ‘mainstream’ areas of the web such as porn sites or gambling sites they can appear on sites that we trust. In the past the BBC, New York Times, Skype, Forbes and Spotify have all had malicious advertising placed on their sites, infecting their users and visitors.
These malicious adverts do not just affect those surfing the web on land, they can also affect any users accessing the internet whilst at sea. Access to a secure network for communications and data transfer if vital at sea and malware is a huge threat, to avoiding being infected by malware though malvertising awareness is key. You will be protecting your own devices as well as the business network.
So what is the purpose of malvertising?
Ultimately the main aim of the malicious advert is to make the hacker money, though in some cases they can be involved in sabotage or espionage.
So why don’t authorities stop malvertising? The simple reason is because they can’t. Hackers are experts at hiding the malicious content and sourcing ways to get it onto the web. There are a number of ways to get malicious adverts on to sites, hijacking the processes used by legal advertisers; paying for ads, compromising an ad network or building their own ad agencies.
- By paying for the ads – paying to post adverts on sites is common practice however hackers hide malicious content in their adverts or direct the visitor to a malicious server to infect them with malware.
- By compromising an ad network – hackers can compromise a legitimate ad network and use it to spread their malicious ads instead. This technique is useful for spreading ads on more tightly guarded websites, just like in the attack against the New York Times, the BBC and other websites discussed in the previous section.
- By building their own ad agencies – This method isn’t as common because it’s a lot more work, but it’s still a possibility. A good example is the 2017 Zirconium attacks, which involved a cybercriminal that created 28 fake ad agencies, and was responsible for delivering an estimated one billion malicious ads.
Malware in Malvertising
The malicious advert may contain one of many types of malware depending on the intentions of the hackers.
- Spyware – can take screenshots, take over the microphone and camera, log keystrokes, and even seek out passwords as well as other sensitive information.
- Ransomware – it searches through the folders and locks down any files that it thinks may be important. Attackers then demand that victims make ransom payments with cryptocurrencies, saying they will send victims a key that can unlock the files if they comply. Even in cases where victims pay up, there’s no guarantee that the attacker will send them the key.
- Trojans –used to give attackers backdoor access to a system, as a vehicle to install other malware on the target, or to steal financial details and other data.
- Bots – Attackers may use malware to recruit slave devices as part of a botnet.
- Cryptojacking – attackers sneakily install crypto mining software on a target’s computer, then use its resources to mine cryptocurrencies like Bitcoin for themselves.
- Adware – Attackers can make money by installing software that displays ads on their target’s computers. Each time an ad is displayed or the user makes a click, the attacker makes a tiny bit of money. Over time, this amount adds up, especially across thousands or millions of computers.
Protect yourself against malvertising
You may think that if the hackers are using legal methods there is nothing that you can do to ensure you are not a victim of malvertising. However, there are a number of ways that you can protect yourself against malicious adverts;
- Install a firewall to help identify suspicious activity – your IT department will no doubt have installed a firewall to protect your vessels network, however you must still be aware of malicious adverts as hackers are always working to get past firewalls.
- Ensure the software you use is up to date – ensure any antivirus software you use is up to date to make sure you are protected from the most current threats.
- Use a safe browser – recent versions of Chrome, Firefox and other browsers have a number of safety features to better protect their users so make sure you use an up to date version of a safe browser if accessing the web. You can check how secure your browser is using websites such as Browserscope or Browserspy and by making sure you are using an update to web browser.
- Be wary of plugins – You should only install the plugins that you absolutely need, and only if they come from well-regarded providers. This means no more unnecessary toolbars clogging up your browser screen and culling all plugins that you don’t regularly use. The fewer plugins you have, the smaller your attack surface area, which reduces the chances of an attacker being able to successfully exploit a security vulnerability in one of your plugins.
- Set Java and Flash to ‘click to play’ – Hackers frequently take advantage of Java and Flash to begin their attacks, make sure you set them to ‘click to play’ so if you visit any sites which have them built in you are in control of them playing (& potentially infecting your network). If you don’t have to, don’t click.
- Install a good AV programme – as with the firewall it is likely that your IT department will have installed a good AV programme like GTSentinel to protect the network. Ensure that you also install a good AV programme on your own devices to protect yourself. This will mean that if you connect them to the network with your own device you will not infect it with malware.
Whilst the above may help protect against malware you are still the best line of defence against an attack so be vigilant, and if in any doubt do not click on adverts. If you see a relevant advert you can visit the website the ‘long way’ by typing in the URL to get you to the correct destination.
Malvertising examples (1)
Here are some examples of malvertising campaigns from the past few years:
The VeryMal campaign
The VeryMal campaign is interesting because it cycled through a variety of evasion techniques as its older methods became less effective. The group first received widespread attention in 2018 when it was discovered using steganography to hide redirection code.
When site visitors encountered the malicious ad, JavaScript would fingerprint them to see if they supported Apple fonts. Those that did were sent to the next step, which extracted code from pixels in the ad’s image.
The characters were drawn out individually, then collated into a string, which navigated to a page that hosted a fake Flash update. When potential victims reached this point, the group made use of social engineering to try and convince them that they needed to download the supposed Flash update.
Of course, it wasn’t really a Flash update, but a type of adware for Mac known as Shlayer. Those who were tricked into downloading it were exposed to unnecessary ads on their computer, which also drained resources and slowed it down.
By the start of 2019, the VeryMal group had switched up its tactics. Instead of hiding redirection code with steganography, it was using ad tags to retrieve a similar payload from Google Firebase.
Ad tags are pieces of HTML code that browsers use to retrieve ads from ad servers. Google Firebase is a cloud-hosted app development platform. The tag requests an entry from VeryMal’s Firestore database, then executes it through JavaScript.
The code is obfuscated to avoid detection, and it fingerprints the target, only proceeding against those using Safari. Suitable candidates are then redirected to the fake Flash update page in the hopes that the attackers will be able to trick them into downloading the Shayler adware.
eGobbler
The eGobbler group was one of 2019’s most prominent malvertisers. In April, the group launched a huge campaign that targeted Chrome on iOS. Versions prior to 75 were vulnerable. According to Confiant, the campaign exposed an estimated 500 million user sessions in only six days.
In another burst from August to September, eGobbler reemerged even stronger. Confiant estimated that this grouping of attacks led to over 1.16 billion compromised impressions. At first, this second campaign seemed similar to the first, but it was actually redirecting WebKit browsers, such as Safari. When the code was de-obfuscated, it was shown to use iFrames to further the attack.
While the first attack mainly affected iPhones, 78 percent of the second iteration targeted Windows PCs. Almost 14 percent targeted Mac OS X, about 7 percent Linux, and 1.1 percent iOS. It made 82 percent of its impressions through Chrome, with just 10 percent via Firefox, 3.4 percent via Edge, and 2.2 percent through Opera.
Malicious ads would forcefully redirect susceptible site visitors, leveraging browser vulnerabilities to take them to attacker-controlled landing pages. Malicious payloads would then be delivered through a content delivery network (CDN).
The affected developers were notified of the attack at the beginning of August. A patch was issued for Chrome several days later. The fixes of iOS 13 and Safari 13.0.1 weren’t released until the second half of September.

References
(1) https://www.comparitech.com/blog/information-security/malvertising/
